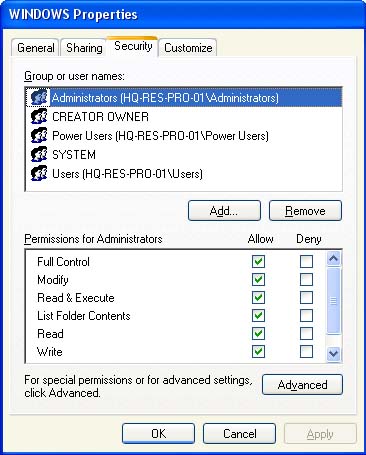
When we talk about system security, we are talking the main components of our environment. Our data and files reside on some systems. Because of that, security of those is important to be maintained. Threat and Vulnerability are inherent to all systems. They are everywhere. One of those is privilege escalation.
Privilege escalation is an exploitation of vulnerability when someone gain privileges other than what originally intended for him. This means that he is able to access the system using other accounts for his benefit. There are two types of it, vertical and horizontal.
Vertical Privilege Escalation
This happens when an attacker uses a vulnerability in the system to gain privileges above what is intended for him. This could be damaging the system or stealing information.
Horizontal Privilege Escalation
This happens when an attacker uses a vulnerability in the system to gain privileges of another user who has the same privilege as him. For example, John and Liz both are users under financial departments. Both have access to payment data. John may attempt to gain Liz access so that he can amend some payment data but the system logs Liz as the one who do it.
How to protect our system from Privilege Escalation
The most common vulnerabilities that can lead to this are Cross-site Scripting (XSS), Improper Cookie handling and weak passwords. These are protection we have to do: