Authorization and Authentication mostly come in pair. Layered upon authentication, authorization is a process to confirm that an authenticated entity has the needed rights and privileges to access and perform actions on resources. It is Access Control job to carry out authorization policy. There are three main access control model used today.
Each has its own advantages and disadvantages. Some organizations may choose and use multiple access control models that fits to their particular systems or environment.
Before we discuss more detail about those, we need to identify the Subject and Object first. Subject is an entity that is requesting access and Object is resource that Subject will act upon. Subject can be a human user or a system process.
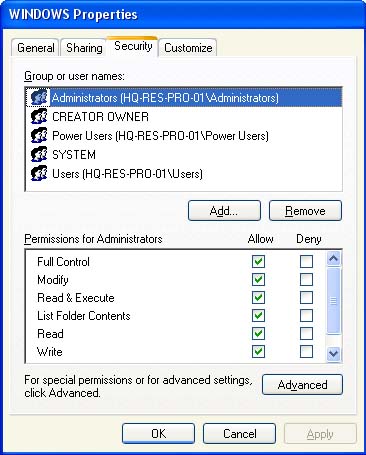
DAC restricts access to objects based on the identity of the subject and is distinctly characterized by the owner of the resource. He/She has right to decide who can access and what level of privileges or rights is given. Usually, it is implemented using Access Control Lists (ACL). The relationship between the individuals (subjects) and the resources (objects) is direct and the mapping of individuals to resources by the owner is what constitutes the ACLs. This method can be integrated with Role-Based Access Control. In this case, we map between user’s roles (as Subject) and resources.
This is an example for Access Control List from Windows.
MAC is based on hierarchical model. Access to objects is restricted to subjects based on the sensitivity of the information contained in the objects. The sensitivity is represented by a level and label. All users are assigned a clearance level and all objects are assigned a security label. In this case, access is determined based on matching a subject’s clearance level with the object’s sensitivity level.
For example, we have data and its categories are top secret, secret, confidential, internal and public. We also have clearance levels are chief department, manager, supervisor and ordinary users. A manager has rights to access all data with secret category and below. Chief department has rights to access all available data. And ordinary users can only access internal and public data.
In this model, access is controlled by the administrator and it can be quite cumbersome to manage. An administrator can quickly become overwhelmed as the systems grow more complex. It is disadvantage to MAC model.
So far, it is common model I used in my systems. Access is given based on roles instead of individual user. And those role are managed by the administrator. The administrator determine all available roles within his organization and then map those to job functions and tasks.
What this mainly provides is that the resource is not directly mapped to the Subject but only to the role. Since individuals can change over time, while roles generally don’t, Subject can be easily assigned to or revoked from roles.
